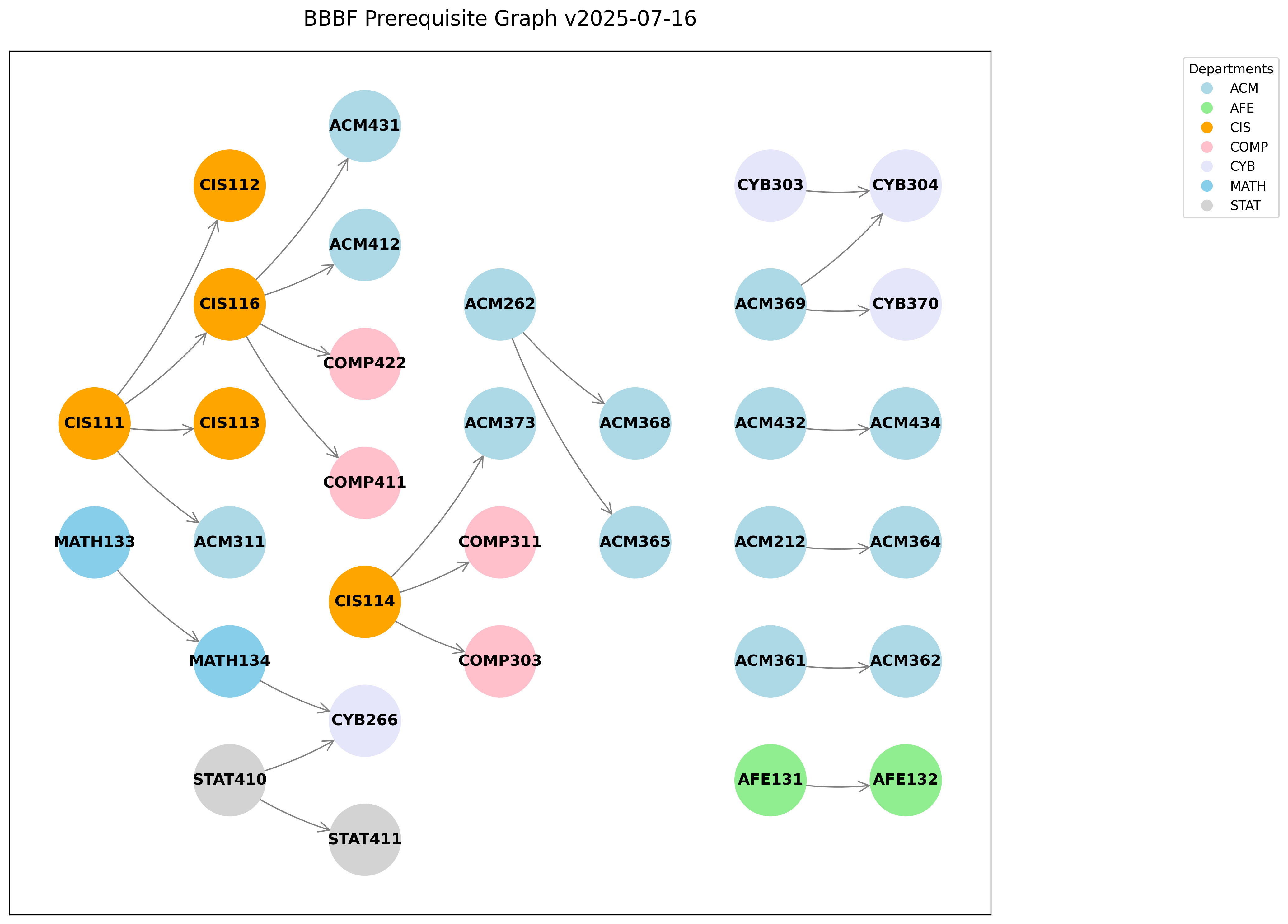
Information Security Technology Courses Configure
1. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| AFE 131 | Academic English I | Core |
| CIS 111 | Software Development Fundamentals | Core |
| CYB 111 | Introduction to Cyber Security | Core |
| ECON 111 | Principles of Microeconomics | Core |
| MATH 133 | Basic Mathematics | Core |
2. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| ACM 212 | Advanced Database Applications | Core |
| CIS 112 | Object Oriented Data Structures | Core |
| CIS 116 | Object Oriented Software Development | Core |
| HUM 103 | Humanities | Core |
| MATH 134 | Advanced Mathematics | Core |
| STAT 410 | Statistics | Core |
3. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| ACM 361 | Networking I | Core |
| CIS 113 | Concepts of Programming Languages | Core |
| CIS 114 | Algorithms | Core |
| MATH 221 | Linear Algebra | Core |
| STAT 411 | Advanced Statistics Applications | Core |
| - | Elective - Core - 1 | Compulsory |
4. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| ACM 362 | Networking II | Core |
| ACM 364 | Database Management Systems | Core |
| ACM 369 | Operating Systems I | Core |
| ACM 474 | Information Systems Security | Core |
| CYB 266 | Computational Random Processes | Core |
| - | Elective - Core - 2 | Compulsory |
5. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| CYB 303 | Cryptology and Cyber Security | Core |
| CYB 370 | Operating Systems Security | Core |
| CYB 422 | Advanced Computer Organization and Assembly Language | Core |
| HTR 301 | History of Turkish Revolution I | Core |
| - | Elective - Free - 1 | Compulsory |
| - | Elective - Department - 1 | Compulsory |
6. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| ACM 363 | Wireless Networks and Mobile Communication Systems | Core |
| ACM 412 | Network Programming | Core |
| CYB 304 | Penetration Tests and Ethical Hacking | Core |
| HTR 302 | History of Turkish Revolution II | Core |
| - | Elective - Free - 2 | Compulsory |
| - | Elective - Department - 2 | Compulsory |
7. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| ACM 475 | Informatics Regulations | Core |
| CYB 394 | Internship | Core |
| - | Elective - Department - 3 | Compulsory |
| - | Elective - Free - 3 | Compulsory |
| - | Elective - Free - 4 | Compulsory |
8. Semester
| Course Code | Course Name | Course Type |
|---|---|---|
| CYB 498 | Graduation Project | Core |
| - | Elective - Extra - 2 | Compulsory |
| - | Elective - Department - 7 | Compulsory |
| - | Elective - Extra - 31 | Compulsory |
| - | Elective - Extra - 4 | Compulsory |
| - | Elective - Extra - 3 | Compulsory |
| - | Elective - Extra - 1 | Compulsory |
| - | Elective - Department - 6 | Compulsory |
| - | Elective - Department - 4 | Compulsory |
| - | Elective - Department - 5 | Compulsory |